
Five of them allow remote compromise of the IoT gadgets, so attackers can intercept video feeds and more.

A Megatrend Challenging Analytical Chemistry: Biosensor and Chemosensor Concepts Ready for the Internet of Things

Fog computing for next-generation Internet of Things: Fundamental, state-of-the-art and research challenges - ScienceDirect

Human Digital Twin in the context of Industry 5.0 - ScienceDirect

Critical IoT security camera vulnerability allows attackers to remotely watch live video - and gain access to networks

Using Images to Detect, Plan, Analyze, and Coordinate a Smart Contract in Construction, Journal of Management in Engineering

Remote-code-execution-via-server-side-prototype-pollution
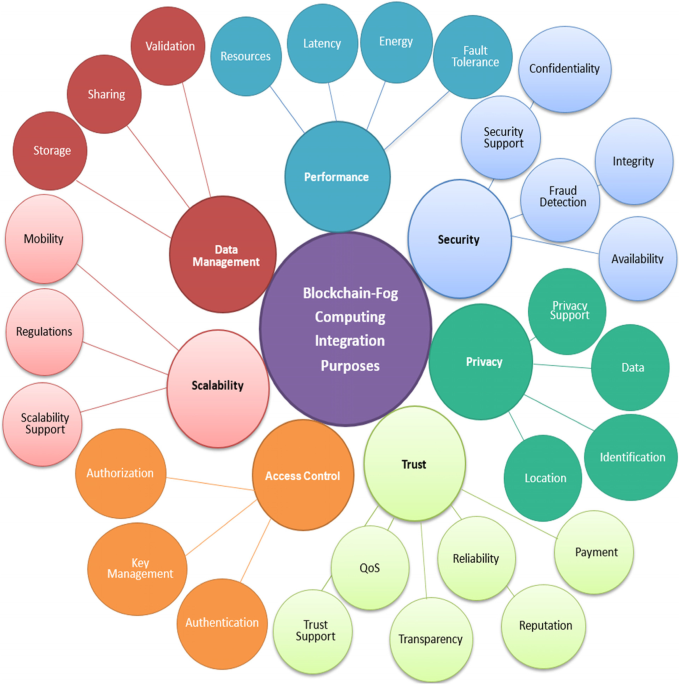
A systematic review of the purposes of Blockchain and fog computing integration: classification and open issues, Journal of Cloud Computing

Warning: New Malware Emerges in Attacks Exploiting Ivanti VPN Vulnerabilities

A Review on the Security of the Internet of Things: Challenges and Solutions
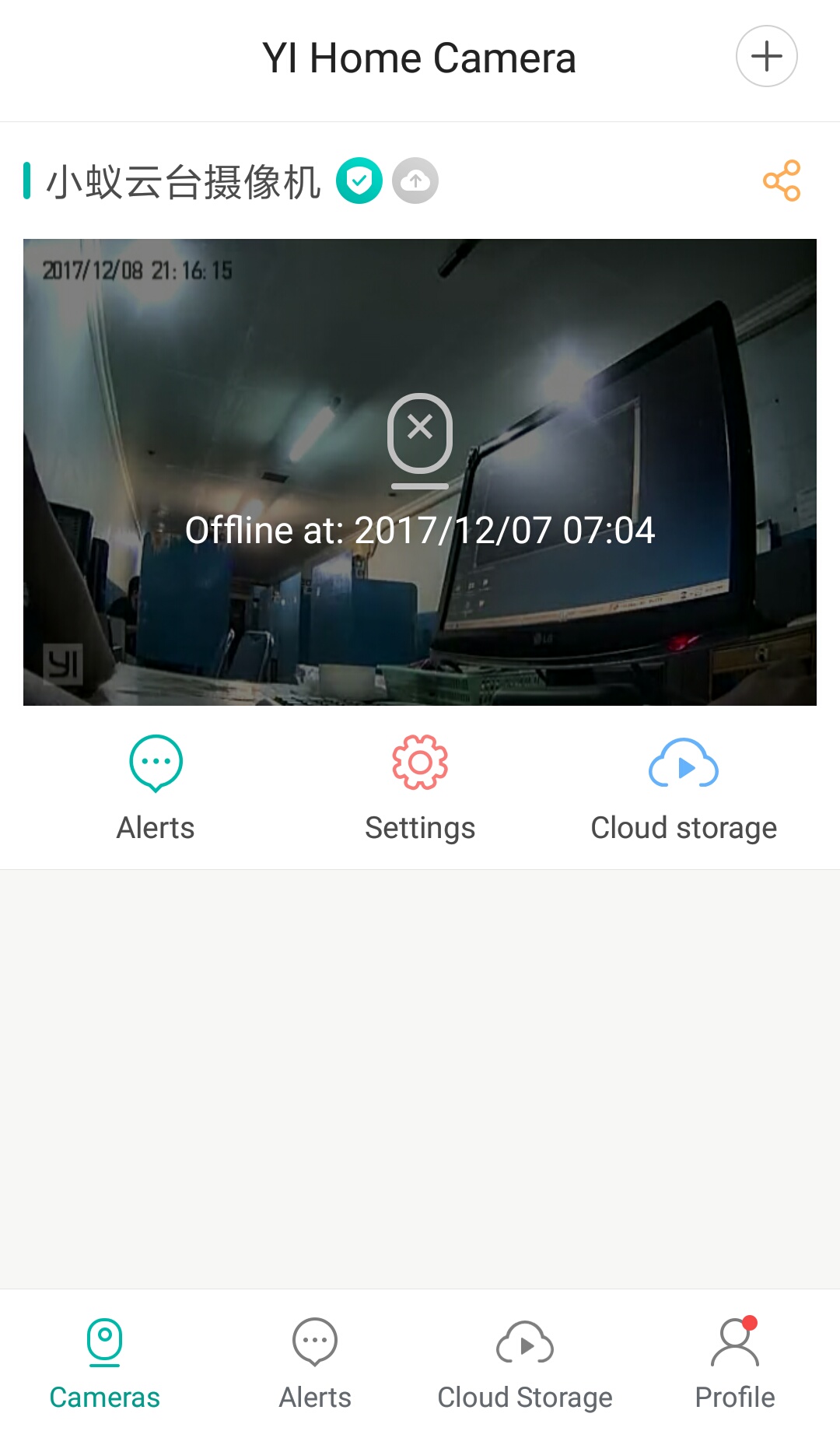
all yi dome camera offline?? · Issue #93 · shadow-1/yi-hack-v3 · GitHub

YI Home Security Camera Privacy Report
Third party software for Yi iot and windows - Community Support - Kami Community

PDF) Architectural Threats to Security and Privacy: A Challenge for Internet of Things (IoT) Applications

Collaborative Cyber Threat Intelligence, PDF, Computer Security







